We live glued to our cell phones. In it are our messages, our photos, our money… and even our identity. That’s exactly why protecting it from hackers is no longer an option, it’s a necessity. But don’t worry: you don’t need to become paranoid or study cybersecurity to keep it safe. You just need to know the weak points… and reinforce them with simple and effective actions.
Here are 10 key tips to shield your mobile against attacks, malware and digital espionage. They are all explained in detail, in a practical way and, above all, with you in mind.
10 tips to protect your mobile from hackers
1. Do not use public Wi-Fi networks without protection
Open Wi-Fi networks are like a party where anyone can enter, watch, copy or steal. You are in a coffee shop, the airport or the subway, you see a free network, you connect… and without realizing it, your information starts to travel without a seat belt.
Hackers can use techniques such as “Man-in-the-Middle”, where they intercept the connection between your mobile and the server you are accessing. The result? They can see passwords, emails, messages and more.
What can you do?
- Avoid connecting to public networks for sensitive transactions such as payments or logging in to your bank.
- If you need to connect, use a VPN (virtual private network). It encrypts your connection and makes it unreadable to third parties.
- Enable the “do not automatically connect to open networks” option in the Wi-Fi settings.
- Disable “file sharing” and Bluetooth if you don’t need it.
A free network can be very expensive if you are not protected. So it is better to be safe than sorry.


2. Install a good antivirus (and don’t ignore it)
Many people think that antivirus is only for computers, but cell phones are just as vulnerable. Fake applications, disguised malware, dangerous links in emails or WhatsApp… all this also reaches the smartphone.
A good antivirus protects you in real time: it detects threats, blocks malicious links and checks the behavior of apps. Some even warn you if your email appears in any data leaks (thank you, massive leaks!).
Recommendations:
- Choose reliable antivirus such as Bitdefender, Norton, Avast or McAfee. There are free versions with basic functions.
- Do not install two antivirus at the same time. They can interfere with each other.
- Enable automatic updates. Threats evolve and so must your shield.
Do not trust: an antivirus is your silent watchman. You won’t see it at work all the time, but when you need it… you’ll want it to be there.
3. Enable screen lock with biometrics
Did you know that 30% of people don’t have any kind of lock on their mobile? If you lose your phone and someone finds it, they can access everything with a swipe of their finger. Alarming, isn’t it?
The screen lock is your first line of defense. The best option today is biometrics: fingerprint, facial recognition or even iris in some models.
Advantages of biometric locking:
- Fast, convenient and difficult to forge.
- No need to remember passwords.
- Works even if your cell phone is stolen while unlocked (many systems can be locked remotely).
Extra tips:
- Accompany biometrics with a PIN or strong pattern as a backup.
- Set up automatic wiping of content after several unsuccessful attempts.
- Avoid simple patterns such as an “L” or a straight line. Surprise the hacker with an abstract drawing.
Protecting the entrance to your cell phone is like putting up an armored door. Let them at least have to sweat to get in.


4. Review and manage the permissions of your applications
Many applications request unnecessary permissions for their operation. These accesses can be used to collect personal data, access the microphone, camera or location without the user noticing.
Best practices:
- Access your system’s settings panel and review the permissions granted by category (location, camera, camera, microphone, contacts, etc.).
- Revoke those permissions that are not essential for the operation of the application.
- Avoid granting permissions automatically when installing new apps.
Controlling permissions is one of the most effective measures to avoid information leaks or unauthorized access.
5. Always keep your operating system updated
Updates are not just about changing the design or adding new functions. Every time you update your mobile system, you are closing doors that hackers could use to get in.
Developers on Android, iOS and other platforms detect security flaws all the time. When one is found, they release a “patch” that fixes the vulnerability. If you don’t update, your phone is left open to known attacks.
What you should do:
- Turn on automatic updates. Don’t let “I’ll do it later” become an invitation for cybercrime.
- Also update applications, especially browsers, banking apps and social networks.
- If your mobile no longer receives updates because it is too old, consider changing it for a newer one. It may seem like an expense, but it is an investment in security.
Remember: if you do not correct the errors in your system, others will do it… but against you.


6. Do not download apps outside official stores
We know: sometimes you get an app via WhatsApp, or you see a supposedly free “premium” version on an external website. But installing apps outside the Google Play Store or App Store is like inviting a stranger to sleep in your house without asking questions.
Apps outside official stores can:
- Carry hidden malware that installs without you noticing.
- Record your keystrokes (keyloggers).
- Activate microphone or camera without real permission.
- Send data to remote servers in unregulated countries.
What you should do:
- Disable the option to install apps from unknown sources (Android allows it manually).
- Check the ratings and reviews of apps in the official stores.
- Even within the store, be suspicious if an app has too many features to be free or has unnecessary permissions.
All that glitters is not gold. And on the web, what seems free is often paid for… with your data.
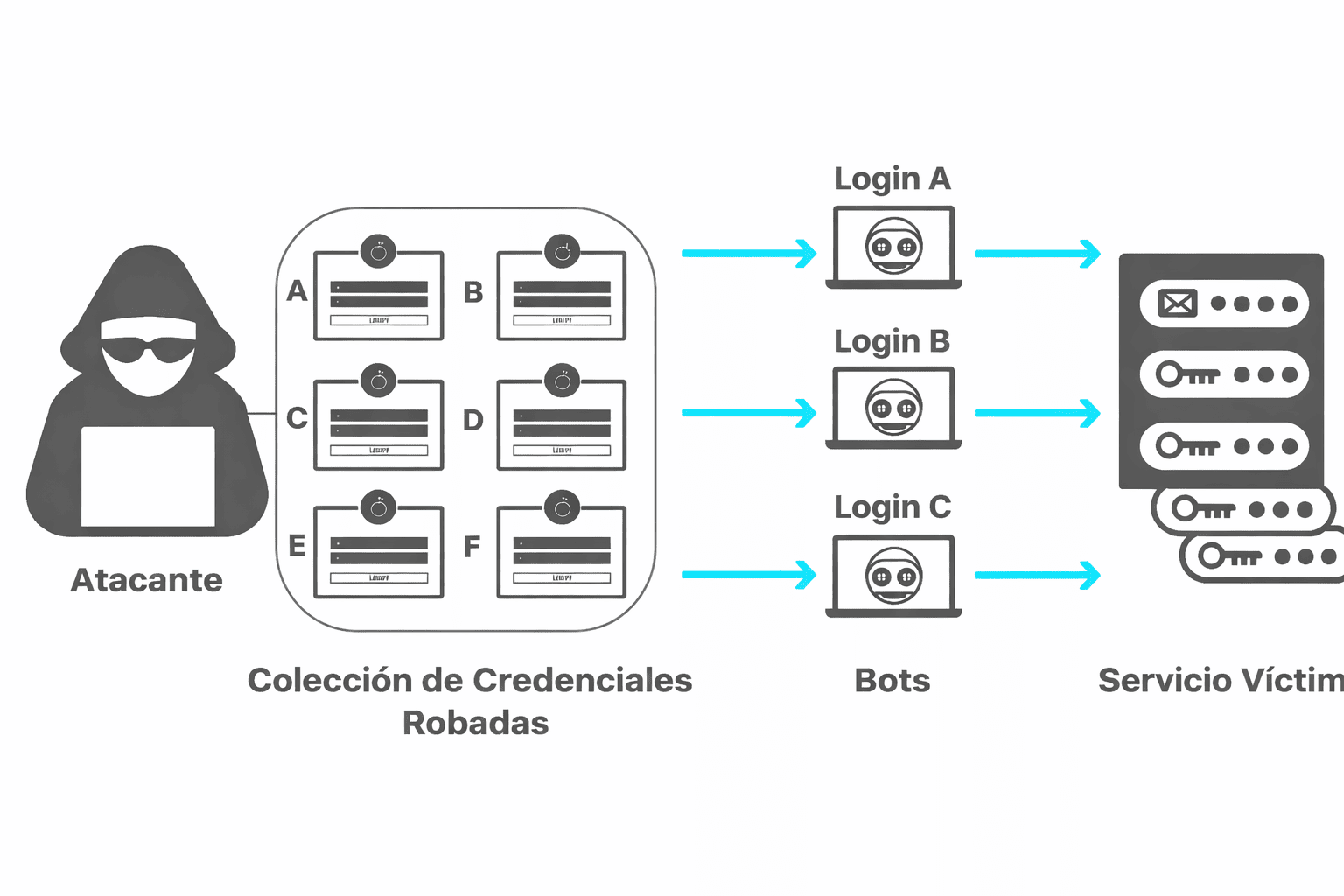
7. Use unique passwords and password managers
If your go-to password for everything is “123456”, ‘yourName123’ or “password”, this tip is for you. Hackers don’t guess, they use lists of millions of common combinations in automated attacks. If your password is easy or repeated, it’s a matter of time before it goes down.
The solution is not to remember 50 complex passwords, but to use a password manager. These apps create and store secure passwords for you.
Best practices:
- Use passwords of at least 12 characters, combining letters, numbers and symbols.
- Do not repeat passwords between services.
- Change the most critical ones (email, banking, networks) from time to time.
Your password is the key to your digital life. Are you really going to use the same one for everything?


8.Enable two-step authentication whenever you can
Even if you have a good password, it is possible that it could be leaked in a data breach. What can prevent you from being hacked in that case? Two-step authentication, also called 2FA verification.
Here’s how it works: when you log in, it asks you for a second proof of identity, such as a code sent to your cell phone or an authentication app (Google Authenticator, Microsoft Authenticator, etc.). Even if they have your password, without this second factor they will not be able to log in.
Activate it in:
- Social networks
- Banking apps
- Cloud storage (Google Drive, Dropbox, iCloud)
Many services offer you this option and we don’t activate it because we are “lazy”. But it is one of the best barriers against account theft.
A password can be stolen. A second factor… complicates things quite a bit for the attacker.
9. Don’t click on suspicious links (even if they look like they’re from your bank)
Phishing is one of the techniques most used by hackers. You get a message by SMS, WhatsApp or mail saying “Update your account now” or “There is a problem with your order” along with a link. You click… and end up on a fake page that steals your information.
Some are almost impossible to spot if you’re not paying attention.
Practical advice:
- Never enter personal data from a link. It is better to enter the site yourself from your browser.
- Check the domain of the link: google.com is trustworthy, but g00gle.com is not.
- If the message has spelling mistakes, exaggerated urgency or threats, be suspicious.
- Do not download attachments from unknown senders.
Remember: your bank will never ask you for confidential information by message. And no legitimate sweepstakes requires you to pay to “claim your prize”.


10. Install a VPN if you are going to connect from public sites
We already mentioned it in the first tip, but it deserves its own space. A VPN (Virtual Private Network) creates a secure tunnel between your mobile and the server you are connecting to. So, even if you use public Wi-Fi, your data is encrypted.
Why do you need a VPN?
- Encrypts your connection: Prevents hackers from intercepting data on insecure networks.
- Hide your IP: Protect your real location and avoid tracking.
- Access blocked content: Useful for services such as Netflix from other countries.
What a VPN does NOT do:
- Does not protect against viruses or phishing (if you download malware or enter a fake website, the VPN will not save you).
- Not all are secure: Some free VPNs sell your data.
- Avoid free VPNs with invasive advertising or without a clear privacy policy. They could be selling your data.
- If you connect a lot away from home, a VPN is an investment in peace of mind. You don’t need to be a techie to use it: install it, activate it and that’s it.
- Avoid free VPNs with invasive advertising or without a clear privacy policy. They could be selling your data.
- If you connect a lot away from home, a VPN is an investment in peace of mind. You don’t need to be a technician to use it: install it, activate it and that’s it.
Are you interested in cybersecurity?
At TRUST lab we share exclusive content, updates and practical tips on digital privacy, data protection and cybersecurity. 🛡️
Subscribe to our newsletter and stay one step ahead.
How to protect your social networks and your digital identity?
In addition to protecting your mobile, it is essential to know how to protect your social networks from hackers. Activate 2FA, use unique passwords and regularly check your account activity. For more complete protection, also review how to protect your information on computers and other connected devices.
Conclusion: Protecting your mobile is protecting your digital life
Conclusion: Protecting your mobile is protecting your digital life
Today your phone knows more about you than many friends. It’s with you all day long, it keeps your secrets, your conversations, your identity. And that’s why it’s a perfect target for hackers.
You don’t need to live in fear, but you do need to be aware. Applying these 10 tips won’t take you more than an afternoon, and can prevent you from losing information, money or even your reputation.
At TRUST Lab we believe that the best security is the one that educates, empowers and accompanies you. That’s why, rather than alarming you, we want to help you act with digital wisdom. This article is a practical tool to strengthen your privacy without complications.
Frequently Asked Questions
Some common signs that your phone has been hacked include: battery draining faster than usual, unknown apps installed, strange behavior (such as calls or messages you didn't make), excessive data consumption and constant heating of the device. If you notice more than one of these signs, change your passwords and scan your device with a reliable antivirus.
Yes, it is possible. Through techniques such as SIM swapping (SIM card duplication) or malicious links sent by SMS, attackers can access your accounts or intercept communications. That is why it is vital not to share your number publicly and to use two-step authentication with apps instead of SMS.
Yes, as long as you download the app from official stores and keep the system updated. Also, avoid connecting to public Wi-Fi networks when accessing your bank, and always enable two-step authentication. Modern banking apps have high security standards, but you should also bring good practices to the table.
Uninstall suspicious apps, change your passwords from another device, activate the security scan with an antivirus and reset the phone to factory settings if necessary. You can also check the permissions granted to each app to detect unusual access to camera, microphone or location.
Follow these 10 steps and reinforce security by activating advanced options according to your operating system.