Why do we keep making the same mistakes?
Cybersecurity has been a priority for years. Even so, every week there is new news about companies being hacked, data being leaked, or systems being paralyzed by ransomware. What is going wrong?
The 5 most common cybersecurity mistakes and how to avoid them
At TRUST Lab, we see it every day: many organizations invest in technology, but they continue to make basic mistakes. Not because of a lack of resources, but because of a lack of awareness, strategy, or simply time.
This article is not meant to point fingers, but to shed light. Because if we know exactly where we are going wrong, we can correct course intelligently and quickly.
Underestimating the importance of internal training
Cyberattacks don’t always start with a sophisticated hacker. Often, they start with a misplaced click.
One of the most common (and dangerous) mistakes is not training the team properly. It’s not just about teaching them how to create secure passwords, but something deeper: cultivating a digital security mindset.
Cybercriminals don’t come in through the door that’s hardest to open; they come in through the one that’s left ajar.
If someone doesn’t know how to identify a phishing email, or doesn’t understand why they shouldn’t use a personal USB drive, technology won’t be able to protect you.
Investing in firewalls and antivirus software is important, but if your team doesn’t know how to behave, you’re building a castle on sand.
Best practices:
- Ongoing training programs, not isolated sessions.
- Attack simulations (phishing, for example) and response analysis.
- Simple and up-to-date internal manuals.
- Area managers who ensure good practices.
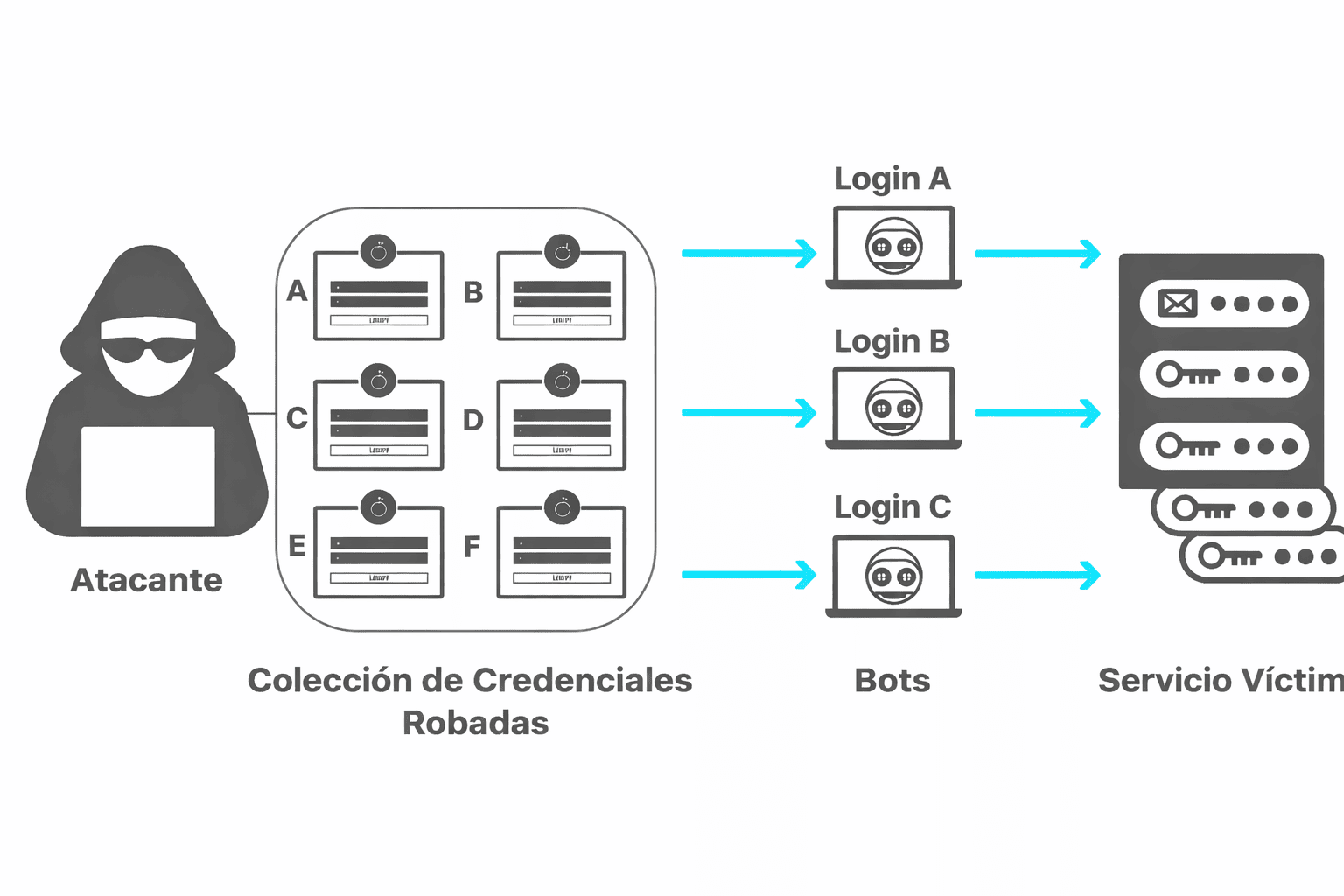
Using weak or poorly managed passwords
It seems unbelievable, but in 2025 there are still companies using passwords such as “admin123” or “Company2024.”
And yes, we know that remembering a thousand passwords is inconvenient… but that doesn’t justify putting the entire organization at risk.
Another common mistake: using the same password for different services, or sharing credentials by email or WhatsApp.
Security starts with the basics, and passwords are the front door.
Solutions that work:
- Mandatory use of corporate password managers.
- Periodic rotation policies (at least every 90 days).
- Enabling two-factor authentication (2FA) on all accesses.
- Monitoring suspicious accesses.
Remember: a single leaked password can open the door to disaster.
Not keeping software up to date
Outdated software is a legal loophole for attackers. Every day, new vulnerabilities are discovered in common programs, from operating systems to WordPress plugins.
If you don’t apply patches in time, you leave cracks that are already public exposed.
Did you know that WannaCry infected thousands of companies because they hadn’t updated a Windows patch that was released two months earlier?
Key actions:
- Automate updates whenever possible.
- Establish weekly review routines for critical systems.
- Monitor manufacturers’ security bulletins.
- Have inventory and patch management tools in place.
Not updating is like having an alarm… without batteries. It may seem like you’re protected, but in reality, it’s already too late.
Not having an incident response plan
Imagine that tomorrow you detect unauthorized access to your servers. What do you do? Who do you call? What information do you need to preserve?
If you don’t have a clear plan, you’ll not only waste time, you’ll lose data, reputation, and a lot of money.
The important thing is not only to prevent the incident, but to know how to act when it inevitably occurs.
Keys to a good response plan:
- Designate an incident management team (even if it is external).
- Simulate crises at least twice a year.
- Establish internal and external communication protocols.
- Document everything that happened for future learning.
Having a plan does not eliminate risks, but it multiplies your ability to react and minimizes damage.
Giving too much access without control
Often, for convenience or ignorance, unnecessary access is granted to employees, suppliers, or temporary collaborators.
The principle of least privilege states that each person should have only the access necessary to do their job, nothing more.
The more unnecessary access you grant, the more doors you leave open to a possible internal or external attack.
Solutions you should implement:
- Regular access audits.
- Elimination of inactive or orphaned accounts.
- Identity management with centralized control (IAM).
- Automatic reviews when changing roles or leaving the company.
Access control is like keys in a building: if anyone can enter any room… you are losing control.
Other mistakes you should also avoid
In addition to the big five, there are other common mistakes that you should keep an eye out for:
- Not performing secure and frequent backups.
- Not encrypting sensitive information, either in transit or at rest.
- Using Wi-Fi without adequate security, especially in small or mobile locations.
- Not performing penetration tests or external audits.
- Not having a clear BYOD (Bring Your Own Device) policy.
Each of these mistakes may seem minor, but together, they can be the Achilles heel of your corporate cybersecurity.

Are you interested in cybersecurity?
At TRUST lab we share exclusive content, updates and practical tips on digital privacy, data protection and cybersecurity. 🛡️
Subscribe to our newsletter and stay one step ahead.
Security starts with the basics
There are no magic formulas. But there is a golden rule: do the basics well, and you’ll be ahead of 90% of companies. The mistakes we’ve seen are not new. But they continue to happen because we often don’t know where to start, or we don’t have the right support. At TRUST Lab, we are here to light the way, share our experience, and help you build a more secure, practical, and human digital environment.
Frequently Asked Questions
The most vulnerable companies are usually small and medium-sized enterprises (SMEs). Not because they have less complex systems, but because in many cases:
- They don't have staff dedicated to cybersecurity; instead, the IT department (if there is one) is responsible for “everything.”
- They do not have clear internal policies on password management, use of personal devices, or remote access.
- They do not provide ongoing training, simulation tests, or awareness campaigns.
- And above all, they do not consider themselves real targets for attack. Many leaders believe that cyberattacks only affect large corporations, when the reality shows the opposite: massive attacks, such as ransomware, are automated and affect large and small companies alike.
A study by the National Cybersecurity Institute (INCIBE) indicates that in Spain, more than 70% of cyber incidents affect SMEs. This is no coincidence: attackers know that SMEs are more likely to have basic configurations, access without two-factor authentication, or outdated software.
The good news is that, with simple and well-implemented measures, many of these vulnerabilities can be closed without large budgets, just with organization, awareness, and support.
The ideal frequency depends on the type and size of the company, but the minimum recommendation is:
- One complete audit per year, reviewing everything from technical configurations to access policies, updates, backups, and incident response.
- In more sensitive sectors (such as banking, healthcare, education, or technology), it is advisable to conduct a partial review every quarter.
- An extraordinary audit should also be conducted whenever there is a major change in the system: server migrations, incorporation of critical software, expansion of the technical team, or after a security incident.
In addition to technical audits, it is important to implement internal drills, risk assessments, and regulatory compliance reviews, such as the General Data Protection Regulation (GDPR) or the National Security Scheme (ENS), if applicable.
An audit is not just a technical review; it is also a tool for learning, prioritization, and continuous improvement. Doing it well and regularly is one of the best investments in prevention.