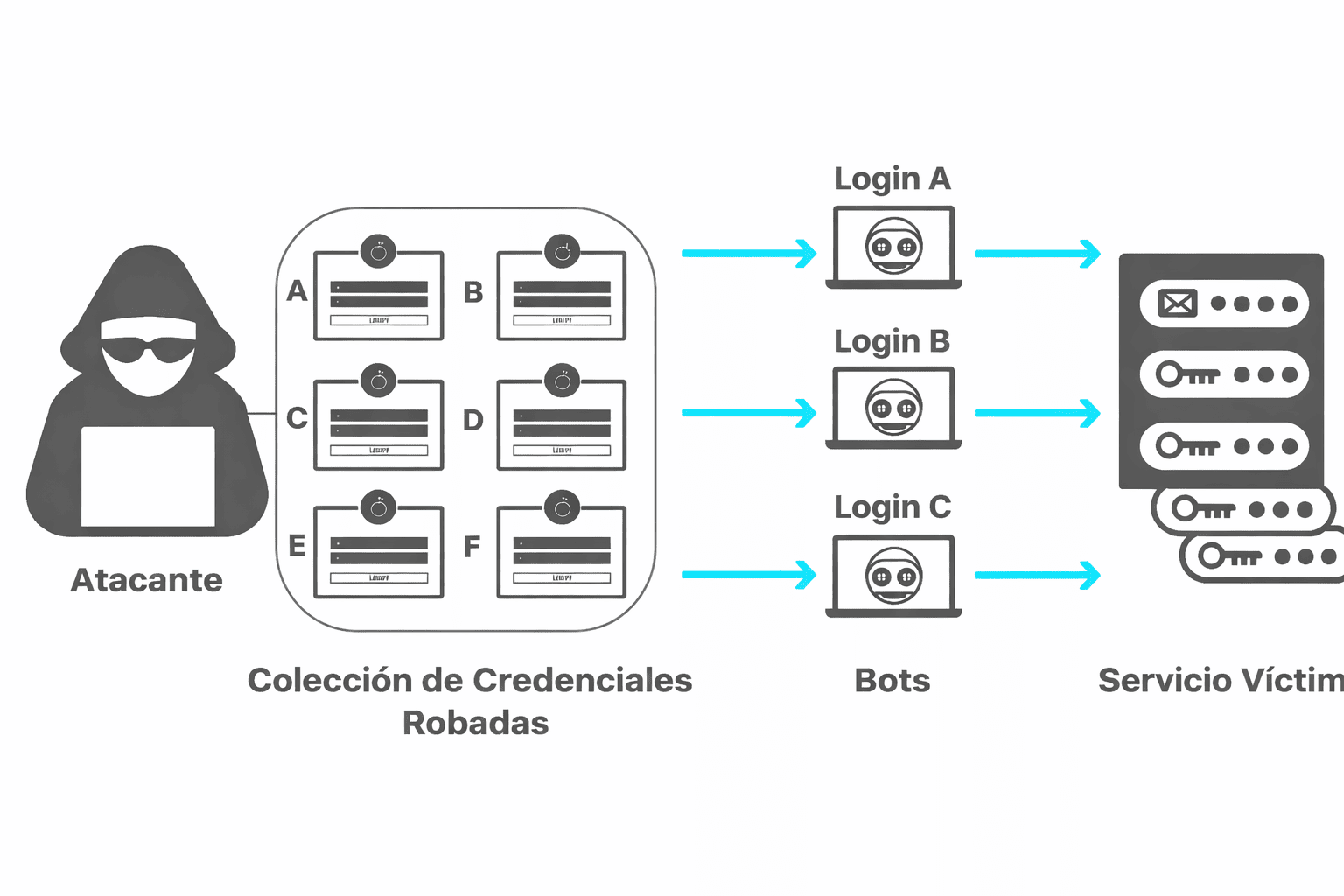
Ransomware is a type of malware (malicious software) specifically designed to block access to a victim’s files or systems, demanding an economic ransom usually in cryptocurrencies in exchange for their release. Its name comes from the combination of two English words: ransom and software.
This type of threat is not new, but it has evolved at an enormous speed. Today, it represents one of the most dangerous, lucrative and sophisticated forms of cyber-attack. It no longer affects only individual users: companies, hospitals, universities and even governments have been victims of ransomware with losses running into millions of dollars.
In most cases, the process is simple but devastating: once the malware manages to infiltrate the system, it encrypts important files and displays a warning message. The attacker demands a payment (ransom) to deliver the decryption key that will allow the recovery of the hijacked information. And there is no guarantee that, after payment, the files will be available again.
This type of attack has become a real business for digital organized crime. There are even ransomware-as-a-service models, where less technical attackers can rent the necessary tools and platforms to launch attacks.
But… how do they get to infect our systems? And more importantly, how can we protect ourselves? Let’s break it all down step by step.
How does a ransomware attack work?
A ransomware attack follows a well-defined and highly effective sequence, in which the attacker looks for a vulnerability, a weakness in the system, a user malpractice or a security breach to exploit and thus introduce the malware. This process usually includes the following phases:
- Infection: Ransomware can arrive in a variety of ways, such as phishing emails with malicious attachments, infected links on web pages, pirated software downloads, compromised USB devices or exploiting vulnerabilities in outdated software.
- Malware execution: Once the infected file is opened or the user clicks on the link, the ransomware executes in the background. In many cases, even before the user notices anything strange, the encryption process has already begun.
- File encryption: The ransomware identifies the most important and sensitive files on the system, such as documents, databases, images and configuration files. It then encrypts them with a strong algorithm (such as AES or RSA), making them impossible to access without the correct key.
- Ransom message: Once the encryption is complete, a message appears on the screen informing the victim of what has happened and demanding a ransom. Typically, instructions to pay are offered (often in bitcoin), with threats to delete the data or increase the amount if not paid quickly.
- (Optional) Data exfiltration: Some modern versions of ransomware not only encrypt, but also steal sensitive information. This allows the attackers to further extort money from the victim: if they don’t pay, they threaten to leak the data publicly.
Types of ransomware: the most common
Ransomware has evolved into multiple variants. Some focus solely on encrypting files; others also lock the system or steal sensitive information. These are the most common:
This is the most classic type. It focuses on encrypting important files. Known examples: WannaCry, CryptoLocker, TeslaCrypt.
Instead of encrypting files, this type completely blocks access to the device. The operating system is rendered unusable and a ransom message is displayed, preventing any further action.
In addition to encrypting, it extracts confidential information. It then threatens to publish it if the ransom is not paid. This makes it especially dangerous for companies with sensitive data.
A growing trend on the Dark Web. Cybercrime platforms rent out ready-to-use ransomware tools, allowing inexperienced attackers to launch campaigns on commission.
It does not encrypt files, but tricks the user with fake threat or virus messages, asking them to pay to “clean” their computer.
¿Te interesa la ciberseguridad?
En TRUST lab compartimos contenido exclusivo, actualizaciones y consejos prácticos sobre privacidad digital, protección de datos y ciberseguridad. 🛡️
Suscríbete a nuestra newsletter y mantente siempre un paso adelante.
How does ransomware spread?
One of the great strengths of ransomware is its ability to spread massively, and there are several common ways in which it can spread. One of the most common is phishing emails, which are fake emails that pretend to be from banks, vendors or well-known services and include malicious links or attachments. This is the most common way used by attackers. Another common way is pirated or infected software, as downloading unofficial software or software from untrusted sources opens a door for infections.
In addition, vulnerabilities in outdated software are one of the main causes, as outdated operating systems, browsers and applications contain security flaws that attackers exploit to infiltrate the system. Removable devices such as USBs can also be a vector of infection, as an infected USB can automatically execute a malicious script when connected to the device. Finally, insecure networks, such as public or misconfigured WiFi, can allow unauthorized access to vulnerable computers. In enterprise environments, it is common for a single infection to spread quickly throughout the network, compromising dozens or even hundreds of machines in a matter of minutes.
How to protect against ransomware
Preventing a ransomware attack is far more cost-effective than dealing with it once it occurs. Here are the best practices:
Perform frequent backups
Save automatic backups, to the cloud or external drives. Disconnect from the network after each backup.
Keep software up to date
Update operating system, antivirus, browsers and all types of software used.
Train employees
Train the whole team in identification of suspicious emails, best practices and incident protocols.
Use reliable antivirus and firewall
Security software must be professional and kept up to date.
Enforce strict access policies
Prevent users from having unnecessary privileges. Implement multifactor authentication.
Audit and monitor constantly
Detecting anomalous behavior early can prevent ransomware from causing serious damage.
Consequences of a ransomware attack
The consequences of a ransomware attack can be catastrophic on technical, financial and reputational levels. The total loss of important files is one of the most serious consequences in the absence of adequate backups. Added to this is the possible operational paralysis, which forces many companies to suspend their activities for days or even weeks, generating significant economic losses, either by paying the ransom, hiring cybersecurity experts or complying with legal sanctions. In addition, the reputational impact can be devastating, with a significant loss of trust from customers, partners and investors. In the most sophisticated cases, ransomware also compromises sensitive data through exfiltration, further compounding the damage. In fact, some attacks have resulted in multi-million dollar damages, shutting down operations and even affecting critical infrastructure such as hospitals or transportation systems.
Is it possible to recover information after a ransomware attack?
Recovering files encrypted by ransomware is not always possible, and that is a reality that we must take into account. Each variant has its own characteristics, and in some cases, there is still no tool capable of reversing its effects. Therefore, the best strategy will always be prevention: having updated and functional backups is key to ensure data recovery and business continuity.
However, if you have been the victim of an attack, here are some useful recommendations to help you evaluate your options:
Check if there is a decryption tool.
You can go to the No More Ransom portal, an initiative supported by EUROPOL, which offers free solutions for certain ransomware variants. You will need to upload one or two encrypted files and the ransom note received to check if a specific solution exists.Do you have recent backups? If you have clean and up-to-date backups, you can remove the malware from the affected devices and restore the data. We recommend that you apply the 3-2-1 strategy: three copies, on two different media, and at least one offline or in the cloud.
Do you use shadow copies of Windows? Windows automatically creates temporary copies called Shadow Volume. If they have not been deleted by the ransomware, you may be able to recover them with tools such as Shadow Explorer.
Explore forensic recovery options. Some specialized forensic analysis software can restore files deleted by malware before encryption. This option may work in very specific cases, but requires technical knowledge or professional assistance.
Keep encrypted files. If you do not have backups and there is no current solution for your case, do not delete encrypted files. New decryption tools are being developed all the time, and may help you later.
⚠️ TRUST Lab does not recommend paying the ransom. Not only is there no guarantee of recovering your information, but it also feeds the criminal cycle that gives life to these threats.
Are you interested in cybersecurity?
At TRUST lab we share exclusive content, updates and practical tips on digital privacy, data protection and cybersecurity. 🛡️
Subscribe to our newsletter and stay one step ahead.
Frequently Asked Questions
The most important thing is to act quickly and with a cool head. Here is a step-by-step guide:
The first thing you should do is consult cybersecurity experts. They can help you contain the attack, try to recover your data and safely remove the malware.
- Disconnect the device from the network (WiFi, Ethernet, Bluetooth) immediately. This prevents the ransomware from spreading to other systems.
- Do not pay the ransom immediately. There is no guarantee that you will get your data back and, moreover, you would be funding the criminals.
There is no guarantee. Paying the ransom does not ensure that the attackers will deliver a working key to decrypt the data. And even if they do, full recovery rarely occurs.
According to a 2024 study, 92% of organizations that paid up failed to restore all their files. Most faced partial loss, data corruption or prolonged outages, even after payment.
Paying may seem like a quick fix, but it's a costly gamble: not only does it fund the crime, it also leaves you exposed to a second attack. The recommendation from cybersecurity experts and international organizations is clear: don't pay and act with a proper response plan.
The difference is in the target and behavior of the malware:
Type of malware | Primary target | Key features |
Ransomware | Economic extortion | files and demands ransom. Sometimes steals data for blackmail. |
Spyware | Spyware | Secretly collects user data (passwords, history, habits). |
Trojan | Hidden infiltration | Disguises as legitimate software and opens the door to other attacks. |
Adware | Ad revenue | Displays intrusive ads and redirects to dubious sites. |
Worms | Rapid propagation | Replicates itself and spreads across networks without intervention. |
Understanding these differences allows you to apply more specific defenses for each type of threat.