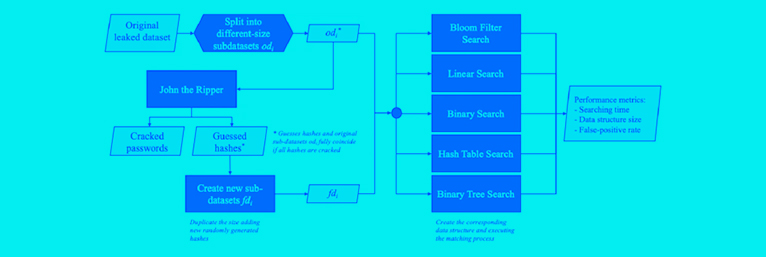
The article proposes the use of Bloom filters to improve the efficiency of password matching. Compared to traditional methods such as hash tables and binary trees, this technique stands out for its low memory consumption and high speed. The results highlight its potential to optimize critical infrastructure systems and reduce credential-related breaches, contributing to a more secure digital environment.

Malicious QR Codes: the New Gateway to Online Fraud
Why QR codes are everywhere (and why it matters) QR codes are used practically everywhere. They’re cheap, easy to create, and easy to scan—just open